Would you like to know what DNS poisoning is? The DNS poisoning method, also known as DNS cache poisoning and DNS spoofing, is a highly sophisticated cyberattack that redirects web traffic between fake servers and phishing websites.
Hackers can use fake sites to trick visitors into sharing sensitive information, as they usually appear similar to the user’s intended destination.
This article will explain DNS poisoning, how it works, why it is so dangerous, and how to prevent DNS spoofing and DNS poisoning vs. DNS spoofing.
What is DNS Poisoning?
The practice of injecting false information into a DNS cache is called DNS cache poisoning because the incorrect response is returned to DNS queries, resulting in users being directed to the wrong website.
There is also a term known as DNS Spoofing that refers to DNS poisoning. IP addresses are the ‘room numbers’ of the Internet that enable web traffic to be directed to the right location.
A DNS resolver cache is often referred to as the ‘campus directory, and when they are incorrect, traffic is redirected to the wrong places until the cached information is corrected.
In the absence of a way for DNS resolvers to verify the data in their caches, incorrect DNS information remains in the cache until the time to live (TTL) expires or until manually removed by the resolver.
DNS poisoning is possible due to several vulnerabilities, but the principal concern is that DNS was designed for a comparatively small Internet based on trust, similar to BGP.
In an attempt to solve some of these problems, DNSSEC, a more secure DNS protocol, has been proposed but has not yet gained widespread acceptance.
How Does DNS Poisoning Work?
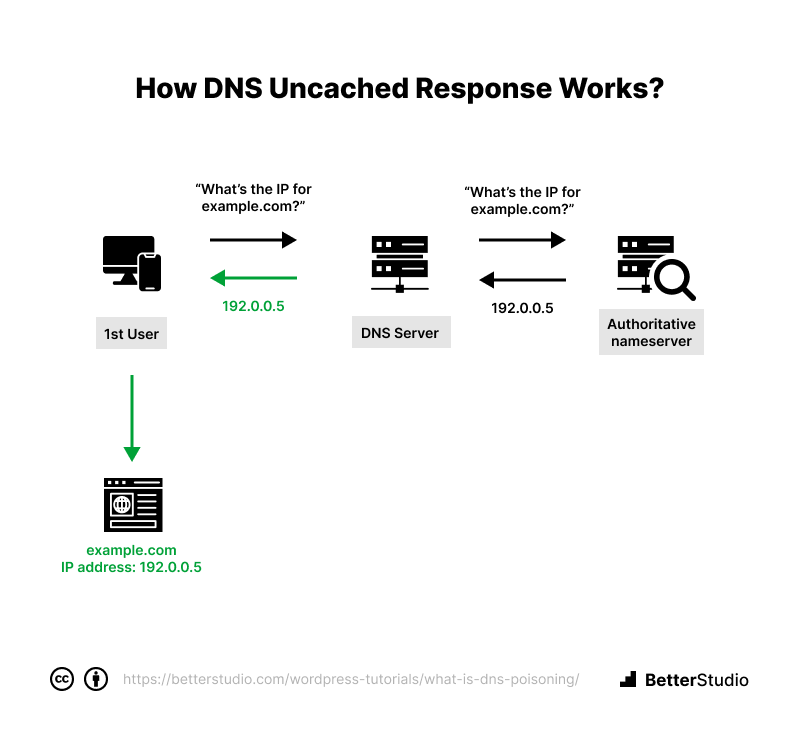
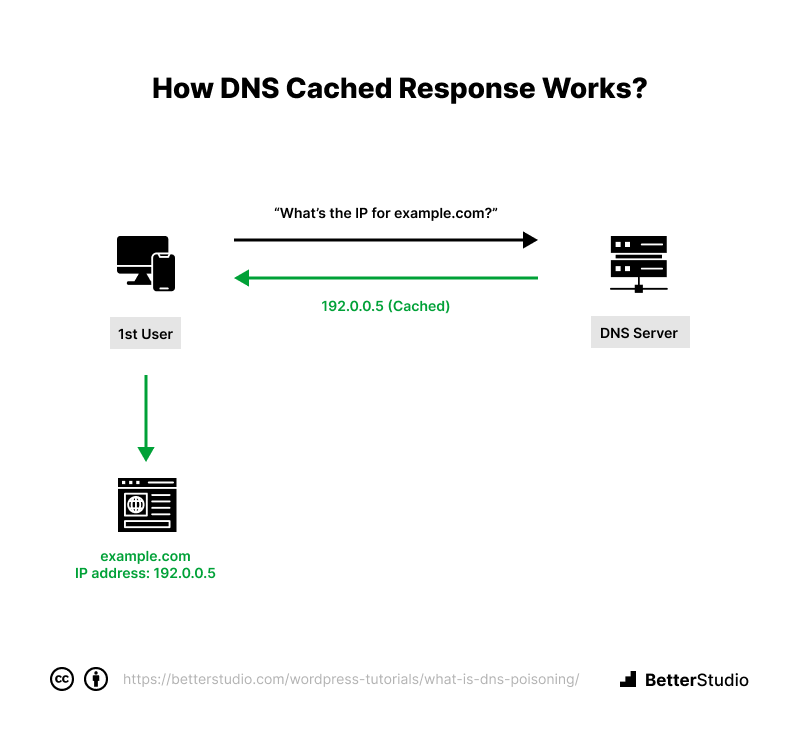
The DNS resolver will store responses to IP address queries for a specific period.
This allows the resolver to respond to future queries more quickly and without communicating with the many servers involved in the traditional DNS resolution process.
A DNS resolver keeps responses in its cache for the duration of the designated time-to-live (TTL) associated with the IP address.
DNS Uncached Response:
DNS Cached Response:
Why is DNS Poisoning So Dangerous?
There are several risks associated with DNS poisoning for both individuals and organizations.
As a result of DNS poisoning, once a device has been victimized, especially DNS cache poisoning, it can become challenging for the device to resolve the issue since it will default to going to the illegitimate website.
The problem of DNS poisoning is further compounded by the difficulty users have in detecting it, particularly if hackers establish fake websites to direct visitors to that look almost identical to the real ones.
When the website is fake, users are unlikely to be aware that they are entering sensitive information without realizing they are exposing themselves and/or their organizations to serious security threats.
Generally, these types of attacks pose the following risks:
Viruses and malware
Users directed to fraudulent websites can be infected with viruses and malware as soon as they have access to those websites.
Many types of malware can be used to access the device and its data, from viruses that infect their devices to malware that provides hackers with ongoing access to their devices and data.
Theft
By using DNS poisoning, hackers can steal information, including login information for secure sites, personally identifiable information such as social security numbers, and sensitive information such as payment details.
Security blockers
Malicious actors can use DNS poisoning as a means of causing serious long-term damage to devices by blocking them from receiving critical patches and updates that strengthen their security.
This approach may make devices increasingly vulnerable over time, allowing them to be attacked by Trojans and viruses and numerous other types of attacks.
Censorship
In the past, governments have interfered with web traffic from their country through DNS poisoning to censor certain information on the Internet.
These governments have effectively blocked citizens’ access to websites that contain information they do not wish to be exposed to through this intervention method.
Examples of DNS Spoofing Attacks
There are various DNS spoofing attack examples. Cyber attackers have used increasingly sophisticated tactics to spoof DNS addresses throughout history.
There is no guarantee that every DNS spoofing attack will look the same; however, a typical DNS spoofing scenario might look as follows:
- An attacker can intercept communication between a client computer and the server computer of the targeted website.
- The attacker can use a tool such as arpspoof to trick both the client and the server into following malicious IP addresses that lead to the attacker’s server by duping both those parties.
- As part of the attack, the attacker creates a fake website in which the malicious IP address routes users to acquire sensitive information about them.
How to Prevent DNS Spoofing
Both DNS spoofing and cache poisoning can be difficult to detect because they can affect both consumer devices and DNS servers at the same time.
Despite this, individuals and businesses can take steps to reduce their risk of becoming cyberattack victims.
These are some ways to DNS spoofing attack prevention:
Never Click on Unfamiliar Links
Malicious websites display fake advertisements or notifications that prompt you to click on a link.
If you click on unfamiliar links, you could expose your device to viruses and malware. It’s best to avoid clicking unfamiliar links or advertisements on a website you usually use.
Set up DNSSEC
DNSSEC stands for Domain Name System Security Extensions, used to verify the integrity of DNS data and the origin of DNS records.
There was no such verification in the original design of DNS, which is why DNS poisoning is possible.
Similarly to TLS/SSL, DNSSEC employs public key cryptography to verify and authenticate data.
DNSSEC extensions were published in 2005, but DNSSEC has not yet been mainstreamed, allowing DNS to remain vulnerable to attacks.
DNSSEC assigns a digital signature to DNS data and analyzes a root domain’s certificates to verify that each response is authentic. Therefore, it is an excellent way to fix DNS poisoning.
In this way, each DNS response comes from a legitimate website.
Unfortunately, since DNSSEC is not widely used, the DNS data remains unencrypted for most domains
Scan for and Remove Malware
Because attackers often use DNS spoofing to distribute viruses, worms, and other types of malware, you should ensure that your devices are regularly scanned for viruses, worms, and other malware threats.
Installing antivirus software will enable you to identify threats and remove them. In addition, you may be able to install tools to detect DNS spoofing if you own a website or DNS server. These systems scan all outgoing data to ensure that it is legitimate.
Use a VPN
Using a virtual private network (VPN) provides an additional layer of protection against online tracking by attackers.
As opposed to connecting your devices to the local server of your internet provider, a VPN connects you to private DNS servers around the world that utilize end-to-end encryption.
The benefit of this is that attackers are prevented from intercepting your traffic, and you are connected to DNS servers that are better protected from DNS spoofing.
Verify That Your Connection Is Secure
It is often difficult to distinguish between malicious and legitimate websites at first glance, but there are a few ways to determine whether or not you are connected to an authentic site.
Using Google Chrome, you will see a small gray padlock symbol to the left of the URL in the address bar.
It indicates that Google has trusted the security certificate of the domain host and that the website is not a duplicate of another website.
Your browser can alert you if you attempt to access an unsecured site. Your connection may not be secure if a message warns you of this.
In this case, it is possible that the site you are trying to access may be a spoof or not have a valid SSL certificate.
One of the more complex types of cyberattacks to detect is DNS spoofing, but you can take steps to protect yourself and your data with various strategies.
Consider installing a reliable antivirus program or virtual private network (VPN) to protect yourself against future cyber-attacks.
DNS Spoofing vs. DNS Poisoning
The effects of DNS poisoning and spoofing are similar but differ in several ways. Users are tricked into disclosing sensitive information in both cases, which results in installing malicious software on the targeted computer.
Users communicating with servers over public wireless networks are at risk of identity theft and data poisoning due to DNS spoofing and poisoning.
DNS poisoning changes the entries on resolvers or DNS servers that store IP addresses. Consequently, users from anywhere on the Internet will be redirected to the malicious attacker’s site if they use the poisoned DNS server’s entries.
It is possible that the poisoning will affect global users depending on the server that is poisoned. A DNS spoofing attack is a broader term that refers to the manipulation of DNS records.
Changing DNS records and forcing users to visit an attacker-controlled site is considered spoofing, including poisoning.
A spoofing attack may lead to direct attacks on a local network in which an attacker can poison the DNS records of vulnerable machines, allowing them to steal business or personal data.
Frequently Asked Questions
In this section, we are going to provide you with some answers to the frequently asked questions:
Domain Name System (DNS) is a system for converting domain names (for users) into IP addresses (for machines).
Each device connected to the Internet is assigned a unique IP address. This address allows other machines to locate the device.
With DNS, users no longer need to memorize long and complex IP addresses but can use simple domain names.
DNS cache poisoning can be detected using data analytics solutions that monitor DNS activity.
There are several indicators of DNS poisoning:
1. An increase in DNS requests from a source that queries your DNS server for multiple domain names without returning a response.
2. A significant increase in DNS activity from a single source to one domain.
1. Don’t click on links that are unfamiliar to you.
2. Clean your DNS cache to remove any data that has been infected.
3. Using a Virtual Private Network (VPN), you can encrypt all your web traffic through end-to-end encrypted servers.
4. You should check your URL address bar for misspellings to ensure that you are being directed to the correct site.
Conclusion
This article discusses DNS poisoning, how it works, why it is so dangerous, how to prevent DNS spoofing and DNS poisoning versus DNS spoofing.
We hope that this article will provide you with helpful information. If you have any questions or comments, please feel free to post them in the comments section.
The latest articles we have written are available on Facebook and Twitter, so we encourage you to follow us there.